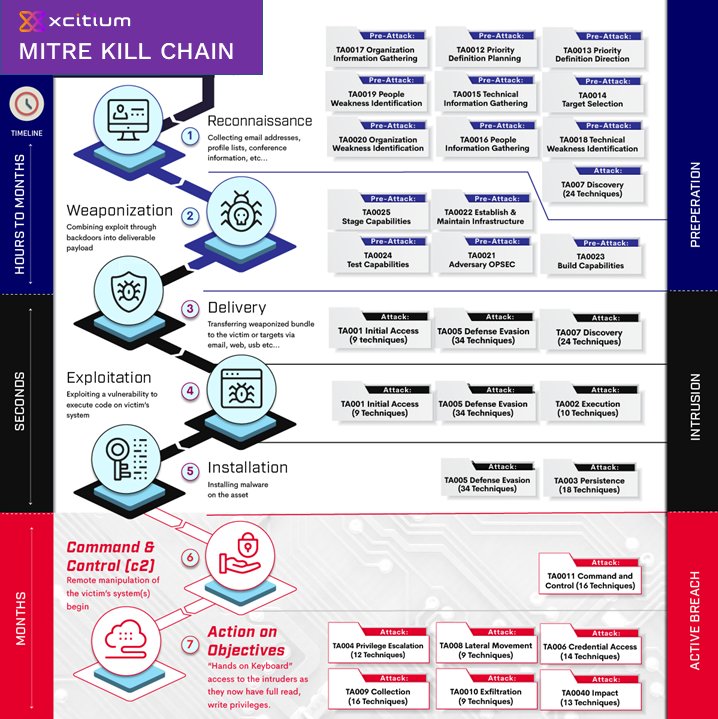
In the constantly evolving landscape of cybersecurity, traditional defense strategies have focused heavily on preventing malicious payloads from entering systems. This approach emphasizes the first four stages of the Cyber Kill Chain: Reconnaissance, Weaponization, Delivery, and Exploitation. While essential, this method often falls short because attackers continually find new ways to bypass defenses. This is where Xcitium’s innovative approach stands out. By focusing on protecting systems even after a payload has been delivered, Xcitium ensures robust security through patented Kernel level API virtualization and Kernel Level Attack Surface Reduction (KLASR).
The Traditional Approach: Blocking Delivery Mechanisms
Traditionally, cybersecurity efforts have been concentrated on preventing the delivery of malicious payloads. This involves:
1. Reconnaissance: Identifying potential threats through monitoring and intelligence gathering.
2. Weaponization: Detecting and mitigating the creation of malicious payloads.
3. Delivery: Employing filters and scanners to block phishing emails, malicious links, and other delivery mechanisms.
4. Exploitation: Patching vulnerabilities and deploying intrusion detection systems to thwart exploitation attempts.
While these steps are crucial, they are not foolproof. Attackers are adept at finding new vulnerabilities and devising sophisticated delivery methods. Thus, no matter how robust these defenses are, some payloads will inevitably slip through.
The Xcitium Approach: Protecting Against Payloads
Xcitium’s strategy pivots from merely blocking delivery mechanisms for payloads to ensuring that once a payload enters, it cannot execute its malicious intent. This is achieved through Kernel level API virtualization and KLASR (Kernel Level Attack Surface Reduction)
1. Kernel Level API Virtualization: Xcitium’s patented technology creates a virtualized environment at the kernel level. This isolates the operating system from any untrusted applications, ensuring that even if a malicious payload manages to enter the system, it cannot interact with the core functionalities of the OS. This virtualization effectively neutralizes the payload, preventing it from causing harm.
2. Kernel Level Attack Surface Reduction (KLASR): KLASR is achieved by introducing a virtualization layer between processes running an unknown executable and Kernel functions. This includes five main virtualization components:
- File System
- Registry
- Kernel Object
- Service
- DCOM/RPC
These components run in both user and kernel mode, handling necessary interrupts and implementing all relevant filter drivers to fulfill requests. By minimizing the attack surface through virtualizing these vital components, Xcitium limits the points where a system can be vulnerable to attacks, making it significantly harder for attackers to exploit any system weaknesses.
Why Xcitium’s Approach is Superior
1. Resilience Against Unknown Threats: Traditional methods rely on identifying and patching known vulnerabilities. However, new and unknown threats can easily bypass these defenses. Xcitium’s approach, on the other hand, protects against both known and unknown threats by isolating them from critical system components.
2. Comprehensive Protection: By focusing on the system’s core through Kernel level API virtualization and KLASR, Xcitium ensures that even if the initial defenses fail, the system remains protected. This layered security approach provides a robust defense-in-depth strategy.
3. Reduced Dependency on Updates: Constantly patching vulnerabilities is not only resource-intensive but also reactive. Xcitium’s proactive defense reduces the dependency on constant updates and patches, offering a more stable and secure environment.
In the realm of cybersecurity, preventing the delivery of malicious payloads is only half the battle. Ensuring that systems remain secure even when these payloads breach initial defenses is crucial. Xcitium’s innovative use of Kernel level API virtualization and Kernel Level Attack Surface Reduction offers a resilient and proactive approach to cybersecurity. By focusing on protecting against payloads, Xcitium provides robust and comprehensive security that adapts to the ever-changing threat landscape.
For more in-depth insights, you can explore the detailed workings of Xcitium’s technologies in these blogs:



