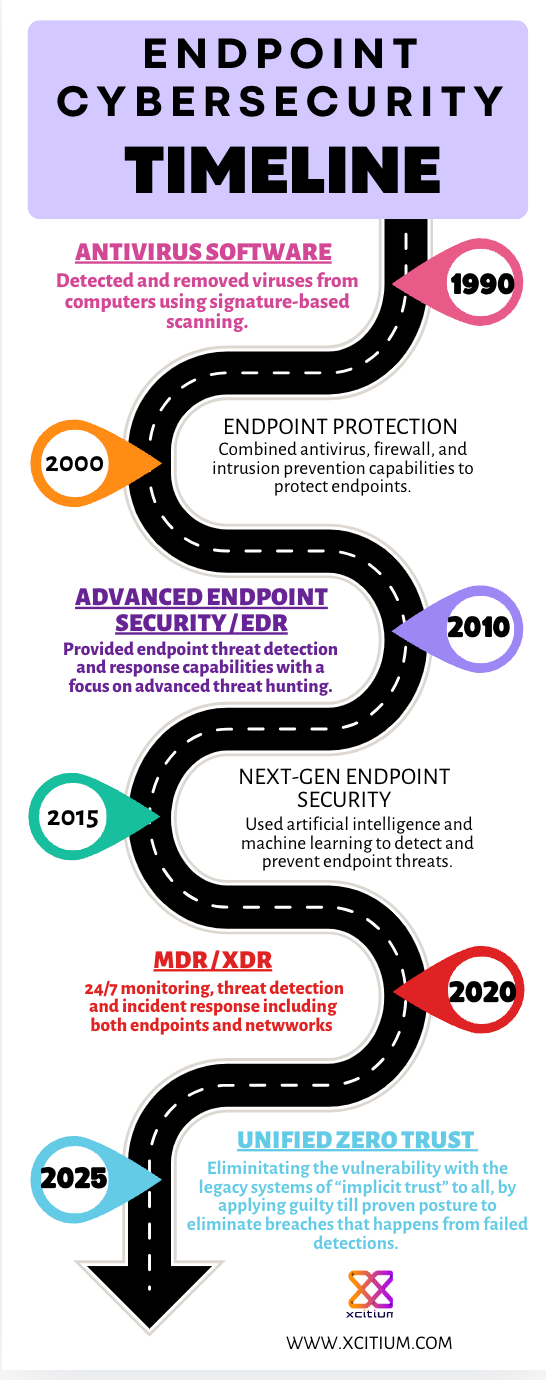
The cybersecurity landscape has changed significantly over the years, evolving from simple virus protection to advanced, integrated systems capable of detecting and responding to sophisticated attacks. In this blog, we’ll explore the timeline of endpoint security technologies, from the early days of antivirus software to today’s cutting-edge Unified Zero Trust platform. We’ll also highlight four distinct platforms that reflect different eras in endpoint cybersecurity architecture and capabilities that should be deployed for best security.
1980s-1990s – AV Platform
The Early Days of Antivirus Software
In the late 1980s, the first antivirus software emerged as a solution to the growing threat of computer viruses. The AV platform was relatively simple, focused on detecting and removing known threats using signature-based scanning techniques. Products like G Data Antivirus (1987), McAfee Antivirus (1987), and Symantec Antivirus (1990) were early pioneers, creating the foundation for what would become modern endpoint security. AVs introduced a new tech stack running on the endpoint.
Capabilities:
– Signature-based scanning: Detects known malware by comparing files to a database of known virus signatures.
– File scanning: Scans system files for malicious software.
– Virus definition updates: Periodic updates to keep the virus database current.
– Basic reporting and alerting: Notifies users of detected threats.
Architecture:
– Client-server architecture: Software runs on the client but reports back to a centralized server.
– Centralized management console: Allows administrators to manage security settings across devices.
– Agent-based deployment: Security software is installed on each endpoint.
Difficulty in building this platform: High
2010s – EDR Platform
The Rise of Endpoint Detection and Response
As cyber threats became more advanced in the 2010s, the EDR platform emerged to address new attack methods that bypassed traditional antivirus. Solutions like Mandiant (2011), Carbon Black (2012), and CrowdStrike Falcon (2013) brought real-time threat detection and response capabilities to the forefront. Unlike AV, which relied primarily on known signatures, EDR platforms used behavioral analysis to detect anomalies and trace malicious activities across endpoints. EDRs required a new tech stack running on the endpoint.
Capabilities:
– Real-time threat detection: Monitors endpoint behavior for malicious activity only for known threats.
– Incident response: Provides tools to remediate when detection fails and breach/infection happens.
– Threat hunting: Allows analysts to search for threats.
– Behavioral analysis: Identifies anomalies based on activity patterns.
– Machine learning: Uses algorithms to adapt and improve threat detection over time.
Architecture:
– Distributed architecture: Collects data from multiple endpoints for centralized analysis.
– Cloud-based management console: Centralized management from a cloud environment.
– Agentless deployment: Some solutions can monitor endpoints without requiring a dedicated agent.
– Integration with threat intelligence feeds: Leverages global data to stay ahead of emerging threats.
– An EDR that has SIEM natively architected and built from ground up is naturally more preferable due to capabilities it offers.
Difficulty in building this platform: High
2015 – MDR/XDR Platform
The Emergence of MDR/XDR
With the advent of EDR the vast amounts of data generated by Endpoint Detection and Response (EDR) solutions quickly became overwhelming for organizations. EDR tools collect detailed logs and behavioral data from every endpoint, often leading to a flood of alerts and incidents that required analysis and response. For many businesses, especially those with limited cybersecurity staff or expertise, managing this deluge of data proved to be an insurmountable challenge. The complexity of analyzing and responding to potential threats in real-time led to missed incidents or delayed responses. This gap gave rise to Managed Detection and Response (MDR) services, which provide expert monitoring and analysis to help organizations make sense of the data, allowing them to outsource detection and response tasks to specialized teams. MDR services became essential for managing the workload EDR generated, ensuring that threats were detected and addressed without overwhelming in-house teams. MDR/XDR platforms are merely cloud based platforms that, in the main, use existing AV and EDR agents, as a result it does not add to the security of endpoint but merely to the management of it.
As security demands grew, organizations began outsourcing some of their cybersecurity responsibilities. The MDR/XDR platform emerged, offering 24/7 monitoring and response services, alleviating some of the burdens on in-house security teams.
Capabilities:
– Integrated threat detection and response: Detects and responds to threats across a wide array of data sources.
– Cloud-based security: Centralized detection and analysis from the cloud.
– Machine learning: Enhanced detection using AI-based analytics.
– Threat intelligence integration: Combines internal data with external intelligence for proactive threat detection.
– Security orchestration and automation: Automates repetitive tasks, such as incident response and threat remediation.
Architecture:
– Cloud-native architecture: Designed for scalability and flexibility in a cloud environment.
– Microservices-based design: Modular components that can be easily updated or replaced.
– API-based integration: Allows for seamless communication between various security tools and platforms.
– Scalable and elastic infrastructure: Can scale to handle large amounts of data, making it suitable for businesses of all sizes.
Difficulty in building this platform: Low
2025 – Unified Zero Trust Platform (UZT)
The Future of Endpoint Security – Unified Zero Trust
Since the introduction of EDR there hasn’t really been a material innovation changing the code running on endpoints, that we call “agent”. With UZT the endpoint agent architecture changes drastically with a whole new tech stack for Kernel level API Virtualization. Today, the Unified Zero Trust platform is emerging as the next evolution in cybersecurity. Xcitium’s Unified Zero Trust Platform exemplifies this shift, focusing on a holistic security approach that integrates endpoint protection, EDR, XDR, CNAPP offering Zero Trust cybersecurity posture from Endpoints all the way to Cloud workloads. Unlike previous platforms, Zero Trust assumes that no file—should be trusted by default. Every file is treated as untrusted and no risk is taken with users’ security by running “assumption based” cybersecurity like EDR or Antivirus platforms do.
Capabilities:
– Integrated endpoint protection: Combines the power of antivirus, EDR, and more advanced defenses.
– Artificial intelligence and machine learning: Enhances the platform’s ability to detect unknown threats.
– Cloud-based security: Uses a scalable infrastructure for real-time threat monitoring and response.
Architecture:
– Cloud-native architecture: Built for modern, scalable environments.
– AI/ML-based design: Leverages AI to improve detection accuracy and automate responses.
– API-based integration: Ensures seamless communication between security tools and external services.
– Identity-centric security model: Focuses on verifying identities, rather than just securing perimeters.
Zero Trust has the extreme difficulty in building because it requires a
-new tech stack of Virtualization,
-new cloud framework of collecting unknown executable files from every endpoint
-new threat labs that can give trusted verdict to every unknown executable file
So in order to create this Zero Trust posture, innovation has to happen both at endpoint and cloud.
Difficulty in building this platform: Very High
Conclusion
The evolution of endpoint security from basic antivirus to the sophisticated Unified Zero Trust platform is a testament to the cybersecurity industry’s ability to adapt to an ever-changing threat landscape. Each platform—AV, EDR, MDR/XDR, and Unified Zero Trust—represents a unique technological leap, offering distinct capabilities tailored to the challenges of its time. As we move forward, Unified Zero Trust is poised to set a new standard for comprehensive security, ensuring that no entity, system, or connection is beyond scrutiny.
For the best security it is absolutely required for any enterprise to run all 3 technology stacks/platforms
-AV
-EDR (for when AV fails)
-ZeroTrust (For when both AV and EDR fails)
Of course based on whether you have the technical resources or not you can add the MDR/XDR platform on top to allow this to be managed by security provider.
Staying informed on these advances is essential for organizations looking to protect their endpoints and adapt to new threats. Whether you’re an enterprise or a small business, understanding and implementing the right security architecture can make all the difference in maintaining a strong cybersecurity posture.



