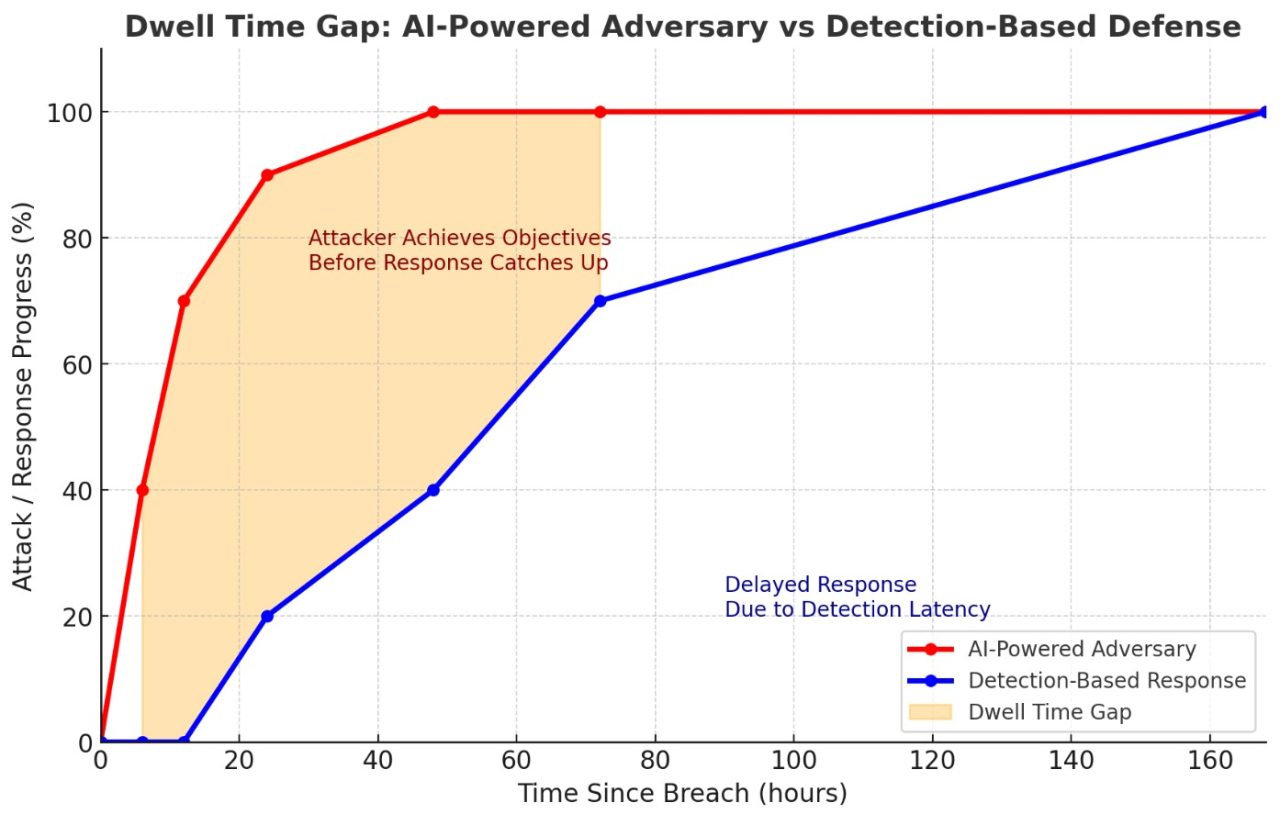
In any legacy, detection-based security model—EDR, XDR, MDR—dwell time isn’t just a historical problem. It’s built into the architecture.
Here’s why it exists now, will continue to exist, and will likely get worse:
- Detection-Based Models Need Observable Evidence
These systems can only trigger once they recognize an indicator—whether it’s a signature, heuristic, or behavioral anomaly. That recognition only happens after the malicious activity has begun. No indicator? No detection. - Adversaries Adapt Faster Than Vendors Patch
With AI now in attackers’ toolkits, they can mutate payloads in real time, obfuscate command-and-control traffic, and dynamically shift behaviors to avoid triggering known detection patterns. This means longer periods before indicators appear, which extends dwell time. - False Positives Create Investigation Bottlenecks
Even when alerts fire, analysts must confirm them before taking disruptive action. AI-driven adversaries can mimic legitimate activity so well that false positive rates climb—slowing down triage and increasing attacker free time. - AI Will Shorten the Attacker’s Timeline, Not Yours
Traditional SOC workflows—detect, validate, respond—don’t get magically faster because attackers use AI. In fact, attackers’ dwell time becomes more productive, as they can automate privilege escalation, data exfiltration, and persistence deployment at machine speed.
The Bottom Line:
As long as your protection model depends on detection before action, you are hard-coding dwell time into your defenses. With adversary AI, that dwell time won’t shrink—it will stretch, because attackers will be better at hiding and faster at exploiting every available second.
The only way to make dwell time truly zero is to remove the dependency on detection before control is applied. Anything else is an exercise in reducing—but never eliminating—the attacker’s free window.



