25. February 2026
Melih Abdulhayoglu’s Blog | Insights on Cybersecurity
Bring to the table win-win survival strategies to ensure proactive domination. At the end of the day, going forward, a new normal that has evolved from generation.
What do top athletes and top salespeople have in common?More than you think. In the world of strength training, real progress doesn’t come from lifting what’s easy.It comes from pushing beyond the point of comfort — from discovering how much more you’re capable of under real pressure. Sales works the exact same way. A professional […]
Assumption: The Silent Killer of Clear Communication In any conversation—whether at work, at home, or in a high-stakes boardroom—there’s one villain that quietly derails outcomes: assumption. It creeps in when someone nods without asking a question, when a leader skips a step because “they already know,” or when a team member hesitates to clarify because […]
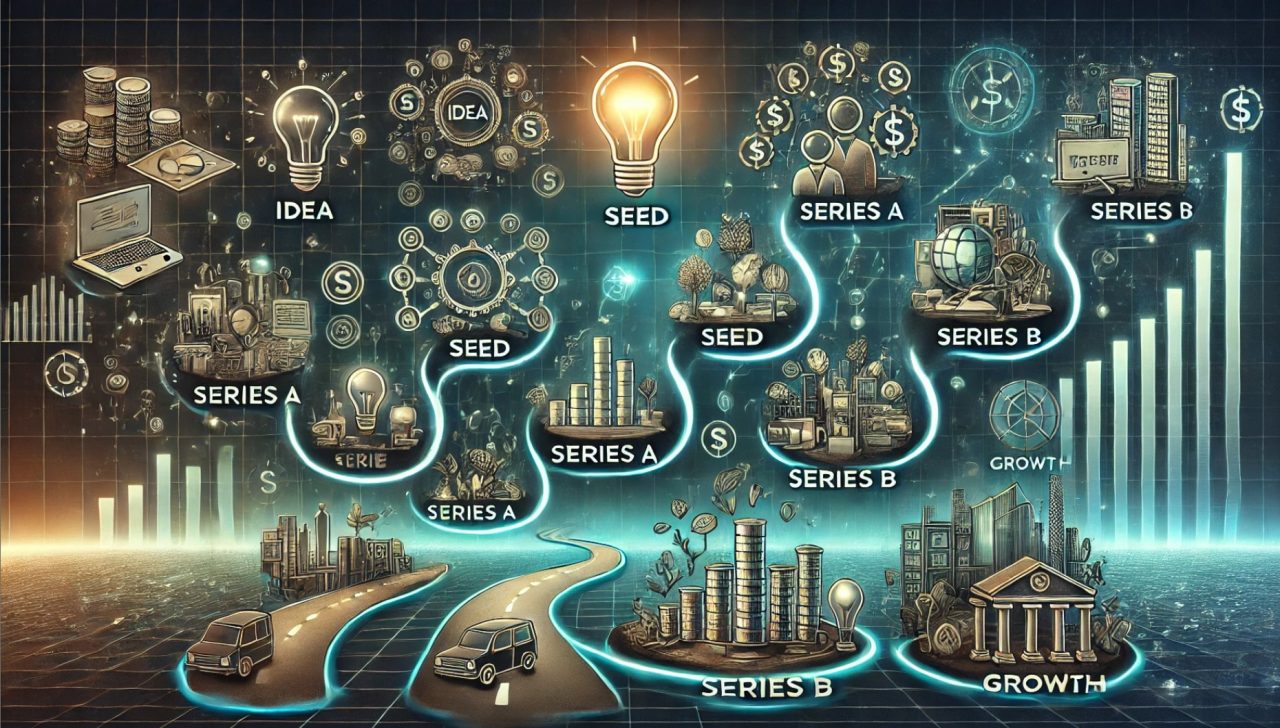
The Fundable Startup: Aligning Product Lifecycle with Funding Stages Startups don’t succeed by simply raising more money. They succeed by systematically reducing risk at each stage, demonstrating that their product and business model are ready for the next level. A great way to think about this journey is by aligning funding stages with the product […]
5min4760
In a U.S. House Committee on Homeland Security hearing entitled “Unconstrained Actors: Assessing Global Cyber Threats to the Homeland,” Adam Meyers, revealed a staggering statistic: “Over the past year, China-nexus intrusions increased 150 percent across all sectors on average compared to 2023. These increases were most significant in the financial services, media, manufacturing, and industrials […]
10min4219
In every workplace, there exist two fundamental types of people: Maximalist Proactive and Minimalist Reactive. These two archetypes approach work, challenges, and growth from completely different angles, and understanding them can reveal a lot about why some companies thrive while others merely survive. The Two Types: Maximalist Proactive vs. Minimalist Reactive Maximalist Proactive Maximalist proactive […]
8min3270
Nature often provides profound lessons about collaboration and teamwork. One such example is how many species require two entities to create new life, highlighting the power of partnership and shared effort. This natural phenomenon mirrors the importance of teamwork in human endeavors—be it in business, education, or personal relationships. Let’s explore why teamwork is indispensable […]
6min3375
In the new Trump Era, Cybersecurity Vendors Are Held Accountable Like Never Before
7min2594
Why Ignorance Is Fueling Ransomware Gangs—and How to Stop It!
9min2173
In the digital age, we’ve grown accustomed to the Attention Economy—a world where platforms and services compete for one thing: our focus. Yet, as technology advances, a new paradigm is emerging: the NuWeb. This vision represents a monumental shift, where the web becomes less about capturing attention and more about fulfilling user needs and intents. […]
10min1760
Imagine standing on the edge of an opportunity that could transform your life. The numbers add up, the timing feels right, and yet, you hesitate. Why? A small, persistent voice whispers, “What if it all goes wrong?” Now, pause for a moment. What if that voice is lying to you? In both business and personal […]