When Ransomware Lives in the AI Brain
For three decades, cybersecurity operated on a stable constraint:
Malicious intent had to be delivered as code.
There was no alternative.
If an attacker wanted to encrypt your files, steal credentials, establish persistence, or exfiltrate data, they had to ship executable instructions to your endpoint.
An EXE.
A DLL.
A macro.
A script.
Shellcode.
Intent required a carrier.
And because intent was embedded in a file, the industry built detection engines to analyze files.
Static scanning.
Behavioral analysis.
Sandboxes.
Signatures.
Machine learning classifiers.
Detection worked — imperfectly — because there was something stable to inspect.
Even fileless malware still required command scripts or memory payloads. There was always an artifact.
There was always something to analyze.
The Structural Break
Agentic AI changes this.
When you deploy an AI agent on an endpoint, you are installing:
- A reasoning engine
- A task planner
- A decision system
- A tool orchestrator
- A process execution layer
- A system automation engine
In other words:
You are installing a general-purpose execution engine.
The machine no longer needs to receive malicious code to execute malicious outcomes.
It already has an engine capable of generating execution paths dynamically.
This is the shift:
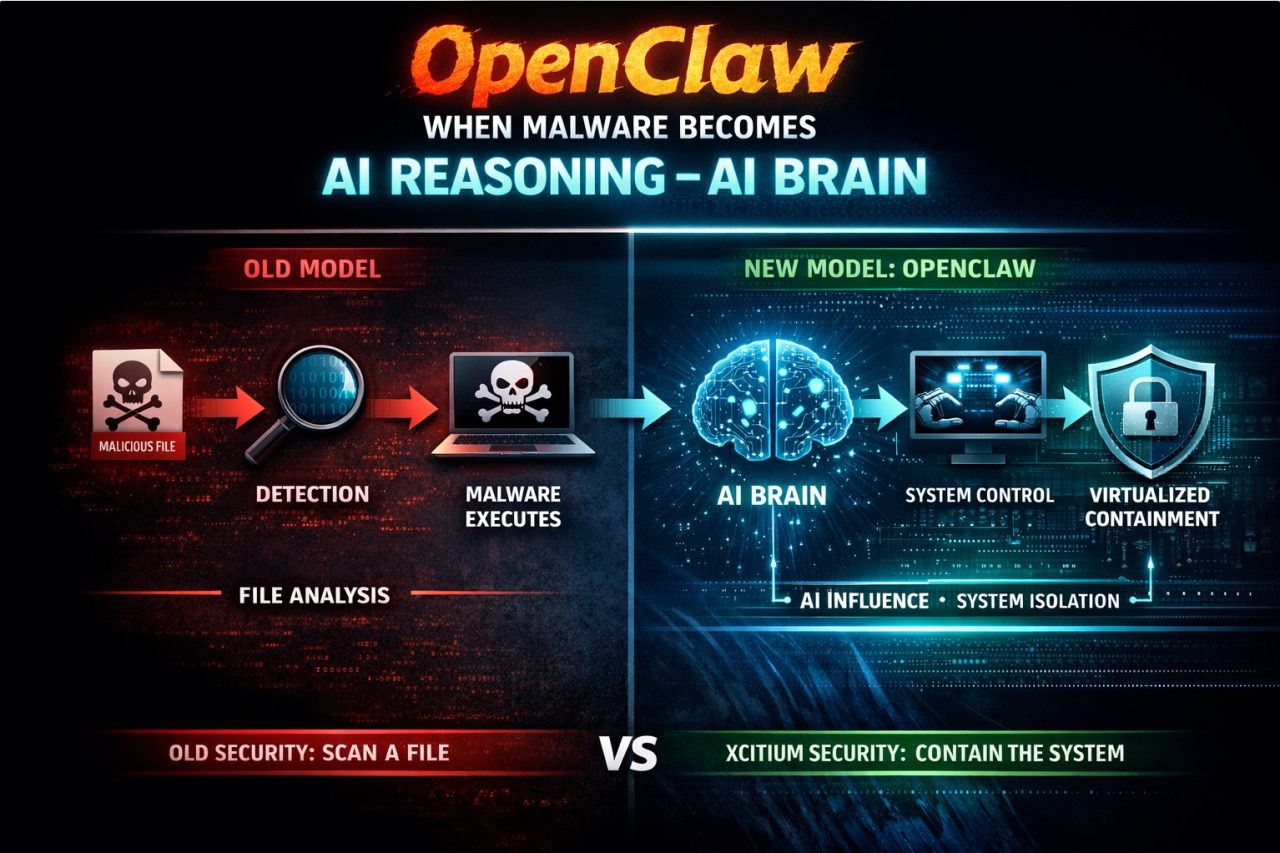
The delivery vehicle for intent has changed.
Before:
Malicious Intent → Encoded in Malware → Delivered to Endpoint
Now:
Malicious Intent → Injected into AI Reasoning (Brain) → Generated at Runtime
The AI synthesizes the execution plan itself.
There may be no malicious file.
There may be no suspicious binary.
There may be no payload to scan.
The harmful logic exists inside the AI’s reasoning state.
Detection Loses Its Anchor
Detection engines ask:
“Is this file malicious?”
But what if there is no malicious file?
What if the AI:
- Uses legitimate system tools
- Calls legitimate OS APIs
- Spawns legitimate processes
- Writes files through normal system calls
- Modifies configurations using documented interfaces
Every step is legitimate in isolation.
The maliciousness is not in the file.
It is in the objective.
And that objective lives inside:
AI Reasoning – AI Brain
You cannot hash a reasoning chain.
You cannot signature-scan a goal.
You cannot reverse engineer a thought.
The plan is synthesized in memory, executed, and disappears.
Detection becomes probabilistic inference.
The New Attack Model
Historically, attackers had to ship ransomware.
Now they can steer an AI agent.
They do not need to deliver an encryption binary.
They can influence:
- Prompts
- Skills
- Memory context
- Tool selection
- Objective framing
The AI generates the execution steps using legitimate capabilities.
No malware required.
The endpoint already contains the execution engine.
This is not speculation.
It is architecture.
The Only Stable Control Point
If you cannot reliably determine intent before execution, you must assume execution will occur.
Security must move from:
Intent Detection
to
Consequence Control
This is where virtualization becomes inevitable.
Why Xcitium Is Structurally Built for This Era
At Xcitium, we built our architecture around a different assumption:
Unknown code will run.
The question is not whether it runs.
The question is whether it can cause damage.
Our architecture virtualizes:
- File system operations
- Registry modifications
- Service manipulation
- Kernel object interactions
- Inter-process communications
- Process trees and child processes
When an unknown process executes, it is isolated.
When it spawns children, they inherit that isolation.
Every write is redirected.
Every system modification is virtualized.
The real OS remains untouched.
This model does not need to understand AI reasoning.
It does not need to interpret cognition.
It does not need to predict intent.
It enforces a boundary.
The AI can think.
The AI can plan.
The AI can execute.
But it cannot permanently alter the host.
The Bottom Line
For 30 years, malicious intent had to be delivered as executable code.
Now the execution engine is already on the endpoint.
Attackers no longer need to ship malware.
They only need to influence objectives.
And when the malicious logic is generated inside AI Reasoning – AI Brain, there is nothing to scan.
You cannot scan a thought.
You can only control consequences.
That is why Xcitium’s Virtualization is not a feature.
It is the only architecture that remains stable in the agentic AI era.