In the world of cybersecurity, precision and transparency are paramount. This brings us to an intriguing issue surrounding Crowdstrike’s Rapid Response Content. At the core of the debate lies the question: Is Rapid Response Content “code” (<– Existential bet)? Crowdstrike argues that it is not. However, an examination of their language and the mechanisms of their system tells a different story.
The Argument
Crowdstrike contends that Rapid Response Content is not code, presumably to avoid breaching the Extended Validation (EV) Code Signing guidelines and Microsoft Kernel-Mode Code Signing requirements. Admitting that Rapid Response Content is code could place them in clear violation of these standards, leading to severe repercussions. This could include the potential revocation of their code signing certificates, resulting in the blocking of all their Windows applications from operating. Such a scenario poses an existential threat to Crowdstrike, jeopardizing their entire operation and standing within the cybersecurity industry. In essence, one simple phrase like “it’s not code” carries existential meaning for Crowdstrike.
Evidence in the Language
1. Behavioral Pattern-Matching Operations
– Crowdstrike states that Rapid Response Content is used to “perform a variety of behavioral pattern-matching operations on the sensor using a highly optimized engine.”
– The key word here is “perform.” In computing, to “perform” often implies executing instructions or code. This terminology suggests that Rapid Response Content functions similarly to code by instructing the system to carry out specific tasks.
2. Content Configuration Updates
– Crowdstrike describes how Rapid Response Content is delivered as “content configuration updates” to the Falcon sensor, involving systems such as the Content Configuration System, the Content Interpreter, and the Sensor Detection Engine.
– The term “Interpreter” is crucial. In computing, an interpreter translates high-level instructions into machine code for execution. By stating that their content is delivered to an interpreter, Crowdstrike indirectly acknowledges that these updates are a form of instructions, script, or code.
3. Flow of Execution
– According to Crowdstrike, the Content Interpreter on the sensor reads the Channel File and interprets the Rapid Response Content. This enables the Sensor Detection Engine to “observe, detect or prevent malicious activity, depending on the customer’s policy configuration.”
– Additionally, Crowdstrike notes, “In other words, Template Types represent a sensor capability that enables new telemetry and detection, and their runtime behavior is configured dynamically by the Template Instance (i.e., Rapid Response Content).” This clearly indicates a flow of execution being modified based on the instructions within the Rapid Response Content. Essentially, this content directs the system’s behavior, much like traditional code.
So, extracting from Crowdstrike’s own language, what they call “Rapid Response Content”:
– Performs
– Uses an interpreter
– Changes the flow of execution
The Duck Test
There’s an old adage: “If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck.” Applying this logic, if Rapid Response Content performs like code, is delivered like code, and executes like code, then it is code.
Regulatory Implications
Recognizing Rapid Response Content as code implies that Crowdstrike may be in breach of:
1. Extended Validation (EV) Code Signing Guidelines
According to the CABForum guidelines: “An obligation and warranty to not knowingly sign software that contains Suspect Code and use the EV Code Signing Certificate as follows: 4.a. only to sign code that complies with the requirements set forth in these Guidelines.” Because the code is dynamically injected after the signing event, none of the code injected into the kernel via Rapid Response Content and Content Interpreter is actually signed.
2. Microsoft Kernel-Mode Code Signing
Microsoft’s guidelines necessitate that any code running in kernel mode is signed and verified to maintain system integrity and security. Because the code is dynamically injected after the signing event, none of the code injected into the kernel via Rapid Response Content and Content Interpreter is actually signed.
The SEC’s Role
Given the potential breach of these guidelines, any new or continued usage of Crowdstrike should be reported to the Securities and Exchange Commission (SEC) as a Material Cybersecurity Incident. Chief Information Security Officers (CISOs) using Crowdstrike products need to be aware of the legal risks and take appropriate action to avoid liability.
Known Vulnerabilities as Material Cybersecurity Incidents
Knowing that you have a known vulnerability in your systems can be considered a material cybersecurity incident if it meets certain criteria. Specifically, the SEC states that if the known vulnerability:
– Poses a significant risk to the confidentiality, integrity, or availability of critical data or systems.
– Could lead to unauthorized access to sensitive information, resulting in data breaches.
– Might cause substantial financial loss or operational disruption if exploited.
– Has the potential to damage the company’s reputation or trust with customers, partners, or stakeholders.
– Results in legal or regulatory implications, including the possibility of fines, sanctions, or mandatory disclosure requirements.
In the context of CrowdStrike’s architectural flaw, the presence of such a significant vulnerability clearly meets these criteria. The ability for unverified content to be executed at the kernel level poses a severe risk to data integrity and system availability. Unauthorized access facilitated by this flaw could lead to data breaches, substantial financial losses, and operational disruptions. Additionally, the damage to the company’s reputation and trust with stakeholders could be immense. Given these factors, when CISOs decide to use or continue to use Crowdstrike, the risk of not reporting this architectural flaw to the SEC as a Material Cybersecurity Incident is too significant to ignore. Failing to report this vulnerability could result in non-compliance with regulatory requirements and a lack of transparency with stakeholders about the potential risks involved.
Conclusion
Crowdstrike finds itself in a legal and ethical dilemma. While the intent to protect their position is understandable, playing with semantics will not suffice. The cybersecurity world demands honesty and transparency. It’s time for Crowdstrike to acknowledge the nature of their Rapid Response Content and address the associated regulatory implications head-on. The world is indeed watching.
References
1. Crowdstrike. “Falcon Content Update: Preliminary Post-Incident Report.” [Falcon Content Update](https://www.crowdstrike.com/blog/falcon-content-update-preliminary-post-incident-report/)
2. Crowdstrike. “Falcon Content Update: Remediation and Guidance Hub.” [Falcon Content Update Remediation and Guidance Hub](https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/)
3. “What is an Interpreter?” [Techopedia](https://www.techopedia.com/definition/1264/interpreter)
4. CA/Browser Forum. “Extended Validation Code Signing Guidelines.” [CABForum EV Code Signing](https://cabforum.org/extended-validation/)
5. Microsoft. “Kernel-Mode Code Signing Requirements.” [Microsoft Kernel Code Signing](https://docs.microsoft.com/en-us/windows-hardware/drivers/install/kernel-mode-code-signing-requirements)
6. CA/Browser Forum. “Extended Validation Code Signing v.1.5.” [EV Code Signing v.1.5](https://cabforum.org/uploads/EV-Code-Signing-v.1.5.pdf)
7. Securities and Exchange Commission (SEC). “Cybersecurity Incident Disclosure Guidelines.” [SEC Cybersecurity Guidelines](https://www.sec.gov/cybersecurity)
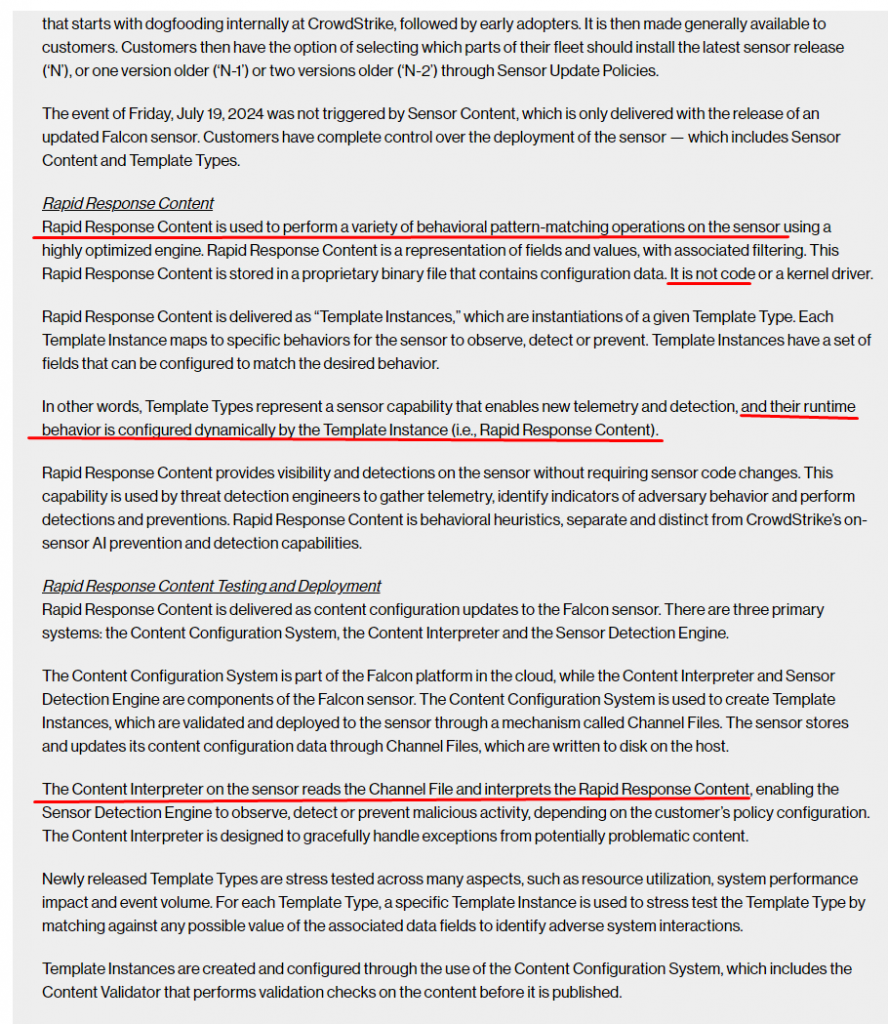
Before the Crowdstrike catastrophe, this is how Crowdstrike was talking about Microsoft’s “Security Culture” being inadequate.
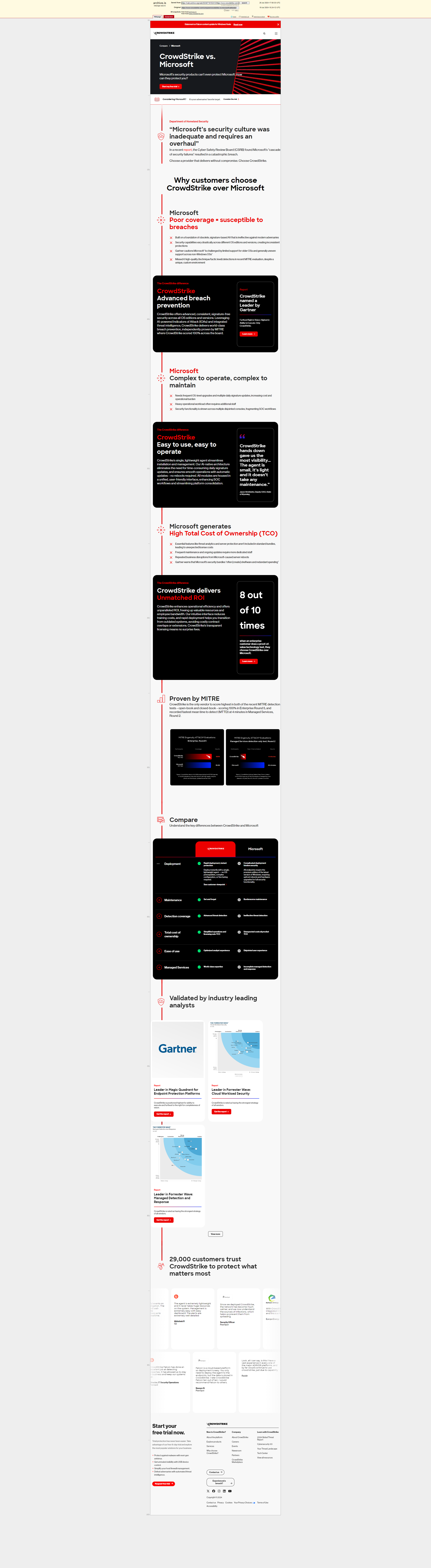
And this is how they changed their tune after the Catastrophe, because clearly their culture is now serious question.