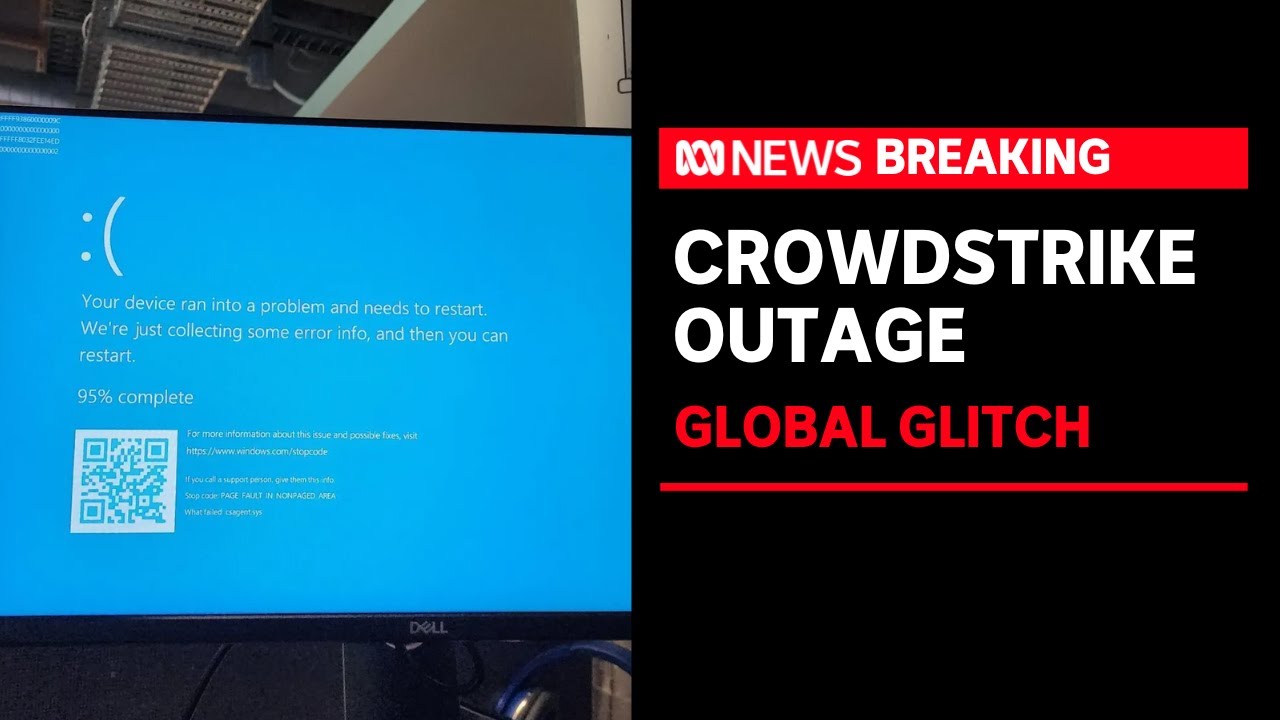
As a fellow cybersecurity leader, I want to extend my sympathies to George Kurtz, president and CEO of CrowdStrike. It’s clear that the challenges faced are not of his choosing, and he must be under significant pressure during this time. Managing a major cybersecurity company is no easy task, and I recognize the dedication required to stay ahead of ever-evolving threats.
In a recent cyber outage that disrupted airports, businesses, broadcasters, and hospitals across the globe, the underlying cause can be traced back to the flawed security architecture of CrowdStrike. This incident highlights a critical flaw in the legacy approach to cybersecurity, which relies heavily on continual updates to kernel drivers—a practice fraught with risks.
George Kurtz provided a crucial insight into the root cause of the problem. He stated: “We are always trying to stay one step ahead of the adversaries, in this case, our systems are looking for the latest attacks from these adversaries that are out there. So this content update went out and as it does and it’s been doing for many, many years…” Here, Kurtz has explicitly pointed out the “root cause” of the problem: the necessity for continual content updates to the kernel, which inherently risks system stability and availability. This is the architectural flaw in these types of legacy systems.
The Dangers of Legacy Cybersecurity Architectures
Legacy vendors like CrowdStrike continue to use an outdated, dangerous, and inefficient architecture that necessitates frequent kernel content updates. These updates are essential for detection-based protection methods but come with significant drawbacks. The process of updating the kernel drivers to counter new threats increases the likelihood of critical failures, such as the widespread Blue Screen of Death (BSOD) incidents recently experienced.
The problem with this approach is threefold:
1. Risk of System Instability: Kernel updates can lead to system crashes and operational disruptions, as seen in the recent outage.
2. Inefficiency: Detection-based methods require constant updates to stay ahead of threats, making it an ongoing race with cyber adversaries. This continuous updating process is resource-intensive and disruptive.
3. Ineffectiveness: Despite the frequent updates, detection-based methods still fail to identify and neutralize emerging threats in a timely manner, leaving systems vulnerable. These kind of legacy vendors admit their ineffectiveness publicly in their own legal documents on their own websites
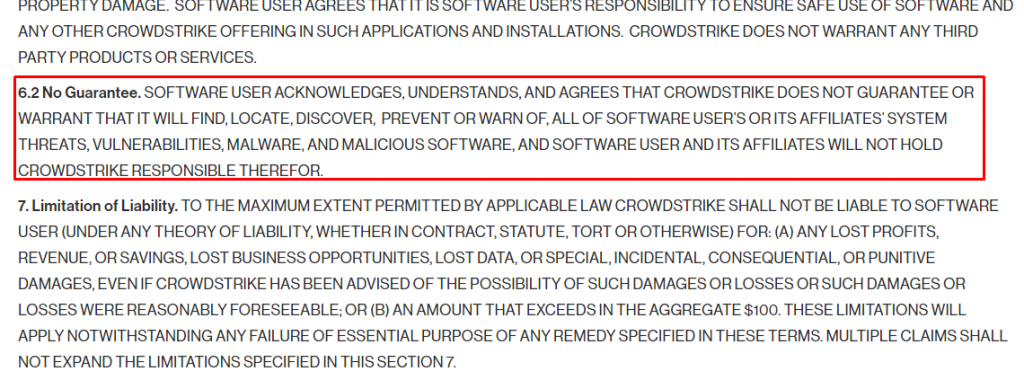
As a result, with these legacy systems, you are playing a Russian roulette of either experiencing a cyber breach because the system is ineffective (which is why cyber breaches are getting more frequent and larger every year), or facing catastrophic crashes (which have been steadily getting bigger and more damaging over the years). If they don’t update frequently, then they fall behind in detection, therefore allowing breaches. These legacy providers are stuck in a vicious circle.
The Long History of BSOD and System Crashes
These issues of BSOD or crashing customers’ computers are not new concepts and have plagued every cybersecurity company using this outdated and flawed architecture for many years. Numerous well-known companies have faced similar issues, revealing a systemic, architectural, problem within the industry.
The Shift to Zero Trust Endpoint Architecture
A more modern and effective approach to cybersecurity is the Zero Trust Endpoint Architecture. This method eliminates the need for continual kernel driver updates by shifting from a detection-based model to an isolation-based model.
As highlighted in a blog by Xcitium, this fundamental shift “eliminates the need for continual kernel driver updates to confront emerging threats.” Other cybersecurity companies, including CrowdStrike, have admitted that continuous updates are necessary to protect against the latest adversaries. This constant updating increases the risk of catastrophic events, as evidenced by the recent widespread BSOD incidents.
Why Zero Trust Is the Future
Legacy cybersecurity companies rely on a method called “detection” to protect their customers, necessitating continual kernel updates—a risky, inefficient, and ineffective method. In contrast, Zero Trust Endpoint Architecture uses a method known as “isolation” to provide protection, avoiding the operational risks associated with frequent updates. By ensuring that no unknown application can have unfettered access to computer resources, risks are drastically reduced compared to legacy detection based systems like Crowdstrike.
Zero Trust operates on the principle that no entity inside or outside the network can be trusted by default. It isolates each application, process, and user session, thereby containing any potential threats within a restricted environment. This isolation ensures that even if an attack occurs, it does not compromise the entire system.
Conclusion
The recent cyber outage attributed to CrowdStrike underscores the dangers of relying on outdated cybersecurity architectures that depend on continuous kernel updates. As George Kurtz’s statement reveals, this legacy approach is inherently risky and prone to causing significant operational disruptions.
Transitioning to a Zero Trust Endpoint Architecture represents a safer, more efficient, and more effective method of protecting systems without compromising their availability. By adopting this modern approach, organizations can safeguard their operations against emerging threats without the perpetual risk of system instability.
For a deeper dive into the pitfalls of continual kernel updates and the advantages of Zero Trust, refer to the detailed analysis on Xcitium’s blog [here](https://techtalk.xcitium.com/2024/07/19/update-trap-how-cybersecurity-vendors-risk-your-operations/).



