Background:
There is a type of certificate called DV certificate. These certificates have a positive security indicator, like a Padlock or “Secure” indicator.
Here is an example of a DV certificate enjoying a security indicator..a green “Secure” with a padlock.
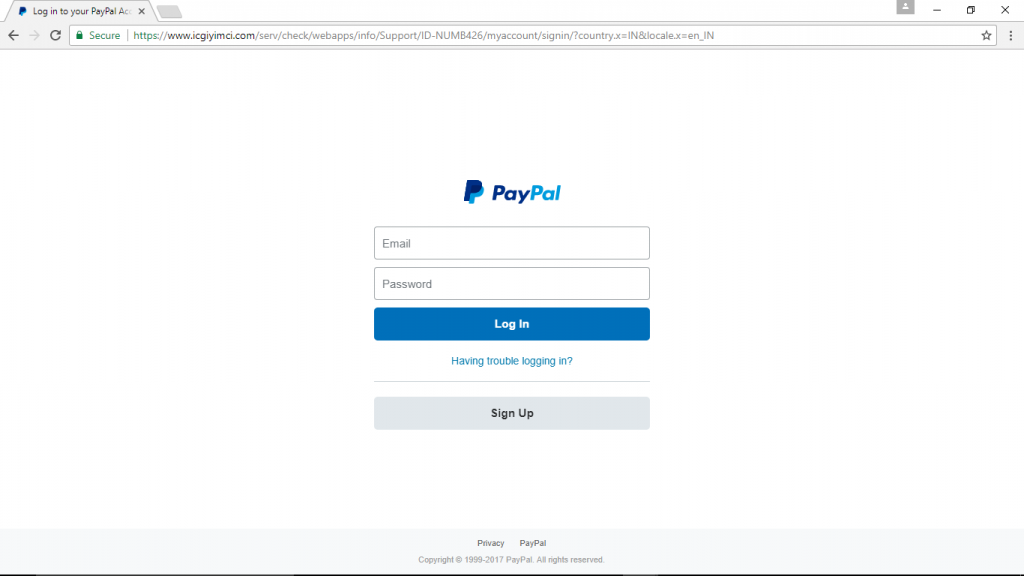
Problem:
As you probably have noticed, this is not a PayPal site. Its a phishing site.
Reaction:
Shame on the CAs who have issued this!!!!
Reaction to Reaction:
Barking up the wrong tree there. CAs are not the blame. CAs don’t choose what to display on the browser. Browsers do. CAs merely provide information. How this information gets displayed is upto the browsers.
So what is the real problem?
The real problem is, process of enchipherment using a DV certificate does not warrant a positive indicator in the browser. Since the invention of DV I have been opposed to the idea of giving DV an indicator, any indicator! Put another way, do the DV process but don’t show any indicator for it.
Hold on there Mr Matey…how dare you!!!! Of course DV provides “Secure Communication”. Look Google Chrome says so:
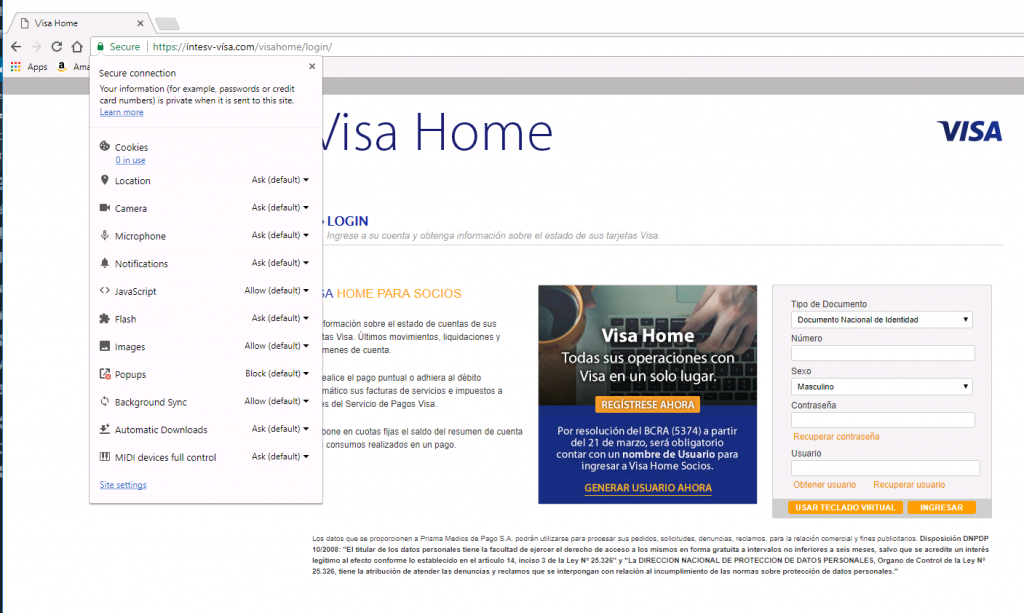
Oh I see….me culpa…Of course it must be secure connection then ……but wait a second.. secure from “who”? (from the phisher in this VISA example?)
Lesson:
Encryption is an exclusion technology. The purpose of Encryption is so that only the intended recipient can read the data being sent. It excludes all unauthorized people. See…told you it was secure connection..So what this means is that my communication with the site was so secure that the People I wanted to avoid were not able to read my communication!
or were they?
Here is the question: How do you know the recipient of your data was not the person who you were trying to avoid in the first place?
Ouch…big problem….can’t answer this question positively…In DV process, I don’t know who the recipient is nor the people I am trying to avoid, so how can I be sure the recipient was not the very person I was trying to avoid? The answer is you don’t know! So how do you know your data ended up with the intended recipient? The answer is you don’t know!
But wait….did you not type paypal.com to go to their site? Surely that tells you, that you are at Paypal.com’s site….erm…no I clicked on the link saying “go to paypal“. So how will I know my private data ended up with the people who I meant to send to in the first place? Can the DV process vouch for that? The answer is NO! Why? Because its not a “Secure” process. Does it not encipher the text. Yes it does. Doesn’t that make it secure? It makes it as secure as you locking your safe and giving the keys to the thief! But the Safe is unbreakable, right….right…but the thief got the key!!!! Although safe is sound “process” is not. It is important who has the key, isn’t it! You simply do not know in a DV case, hence cannot say its secure, because you cannot attest that the “Encryption Process was fullfilled” by making sure only the “authorized person” had access to it. Keys are not people…key holders are…. You can say the text is enciphered. You can say only the matching key can decipher the enciphered text. But calling it “Secure” or giving it any positive indicator is misleading and damaging to user ecosystem.
Here are some thought experiments about the definition of Encryption:
First lets see how Encryption is defined…
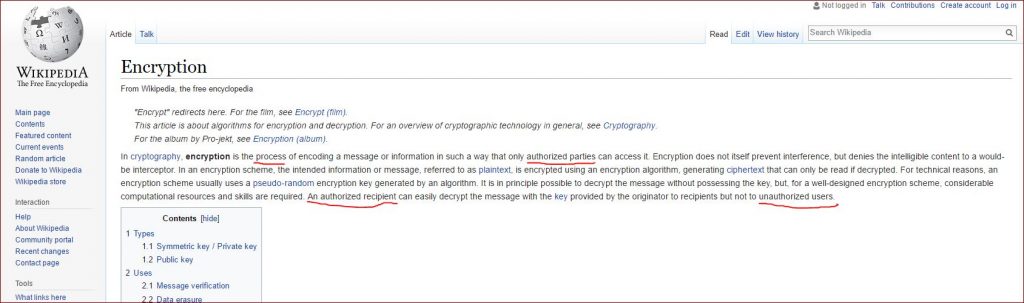
“encryption is the process of encoding a message or information in such a way that only authorized parties can access it”
Does that mean if “the process”..lets call this process the “DV Process” cannot guarantee that only the “authorized party” had access to the data, the process of encryption is not fulfilled? Could you, in fairness, state that “Encryption process” as defined above is fulfilled if you cannot vouch that only authorized parties had access to your data?
Some say, yeah but only the matching key can decipher the enciphered text, therefore it is assumed that the “authorized party” did have access to it. Is the key the key holder?
Who is the “the authorized party” the key or the key holder?
Can a system designed to stop at Key vs Key holder level can ever be called Secure? What is the definition of “Secure”….you are securing something from someone? Who is that someone? is that “someone” the “key” or the “key holder”? For you to call something “Secure”, knowing that it must be secured from someone, without knowing who that someone is, or who ended up with your data, it creates a challenge to call it “Secure”. Is designing an encryption system that stops at key and not at key holder, like playing a football game without the football and at the end saying you had such a good football game? Is it like calling the engine, a Car? How do we define a “Key Holder”? What is “Identity”? Is Domain an “Identity” or mere marker for an identity? I can identify my friend John with his freckles, but these freckles are not his identity but merely marker for his Identity. Is Domain name a freckle for a legal entity/identity? What is the legal definition of “Identity”? Is CPU serial number an “identity”? Technical Identity vs Legal Identity? What are users thinking when they view their world? Are they looking at the world with Technical glasses or everyday glasses of the legal framework?
Is deciphering the text for a matching key like the FedEx driver delivering the package in pristine condition and dropping it at the curb side? Is his job complete although recipient didn’t receive it? What will the FedEx driver say, when confronted by the irate customer who has been waiting for his parcel to arrive? Look, there was no accidents or any issues with the package during transit and I dropped it safely at the curb side!. Of course like encryption process not being fullfilled, neither is FedEx delivery. Unless of course you would like to redefine what “FedEx” delivery is…..in which case the definition of “Encryption” must be re-written removing the word like “Key holder”, “Who”, “Parties”, “Users” or “Authorized Parties” from its definition.
These are thought experiments designed to encourage the reader experiment and think deeper into the definition of “Encryption”, “Identity”, “Secure” and so on. These words deserve our full understanding of their true meaning and definitions.
Again: I am NOT against the DV process. It has its uses. I am against giving DV a security indicator for the protection of end users. It should be neutral!



