25. February 2026
Melih Abdulhayoglu’s Blog | Insights on Cybersecurity
Bring to the table win-win survival strategies to ensure proactive domination. At the end of the day, going forward, a new normal that has evolved from generation.
10min3238
In an appointment-driven sales model, understanding the journey of a qualified lead through the AIDA (Attention, Interest, Desire, Action) framework is crucial for both marketing and sales teams. Each team plays a specific role in guiding potential customers from initial awareness to the final purchasing decision. Let’s break down these responsibilities and clarify how each […]
9min4913
In the realm of sales, strategies and methodologies play a pivotal role in achieving success. One of the fundamental debates in sales management revolves around the choice between activity-based and outcome-based approaches. Each method has its merits and drawbacks, but understanding the nuances between them can significantly impact sales performance and overall business outcomes. Activity-Based […]
1min14755
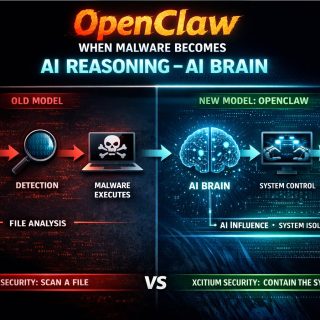
What is Malware/Ransomware? Malware/Ransomware is a legitimate code (within context of the CPU instructions) doing illegitimate things. So Code is legit because CPU understands and executes the code/instructions in this executable file that we call malware/ransomware. However what this code/instructions do is bad stuff for us… What is Malware/Ransomware Problem? You executing/running this malware/ransomware! If […]
4min15164
There are, in the main, two security postures in Cyber Security: 1-Allow ALL, deny BAD 2-Allow Good, deny REST Today the vast majority of cybersecurity world works with: (1) Allow ALL, deny BAD They try to Deny BAD by trying to detect it by using AI,ML, Heuristic, Behavior Analysis, EDR. I must say, the […]
3min30992
Its 10pm night time…..someone knocks on your door…you answer the door….a total stranger……you invite this stranger in…….ask him to sit on your sofa……he is sitting there……it now has been 24 hours….this stranger is still sitting on your sofa… Can you say he is a good guy? Of course not! Absence of bad behavior does NOT […]
2min28241
A Software is made up of instruction set, that we call a piece of “Code”. A programmer writes this code and once compiled and packaged becomes, Software/Application. When you launch this Application/Software, the code is sent to CPU for those instructions to execute. For example this piece of Code could be instructing the CPU […]
3min21424
As a tech incubator and a CEO one of the most important tasks I have is to train, educate and arm people with the ability to continually improve their tasks. How do I teach this to them? Is there a structure, process or formula for this? Over the years, I had to create one. Here […]
4min11201
EndPoint Protection: (AV, NGAV, EPP etc) Is like your doors, windows, gates that protect your property. It stops unwanted people from coming into your home. What to look for in Endpoint Protection: There are two main types of methods Detection based: These kind of systems have to be able to “identify” bad behaviour to […]
8min12735
As human beings, how do we determine if information given to us is good or not? We as the human race “Trust” or “Not Trust” the messenger (channel) of the information. Its more efficient and easier to trust the messenger than analyzing the content. Human brain does not (in the main) analyze the content to […]