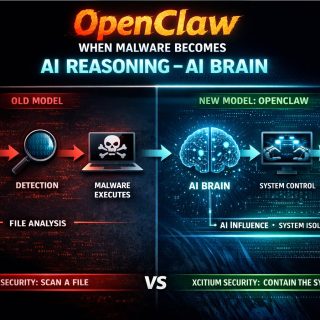
03. March 2026
Author: Melih Abdulhayoglu
7min2878
Lessons from the Car and Aviation Industries In industries like automotive and aviation, transparency is key to maintaining trust and ensuring safety. Historical performance data is readily available, allowing consumers to make informed decisions based on past performance. Cybersecurity, however, remains shrouded in secrecy, even as it plays a critical role in protecting sensitive data […]
7min4491
In the fast-paced world of business, effective communication is paramount. Misunderstandings, delays, and inefficiencies can lead to frustration and hinder productivity. One common scenario where these issues arise is in prolonged email threads. To address this, I advocate for a simple yet powerful principle: The 3 Email Rule: By limiting email threads to three exchanges […]
15min3288
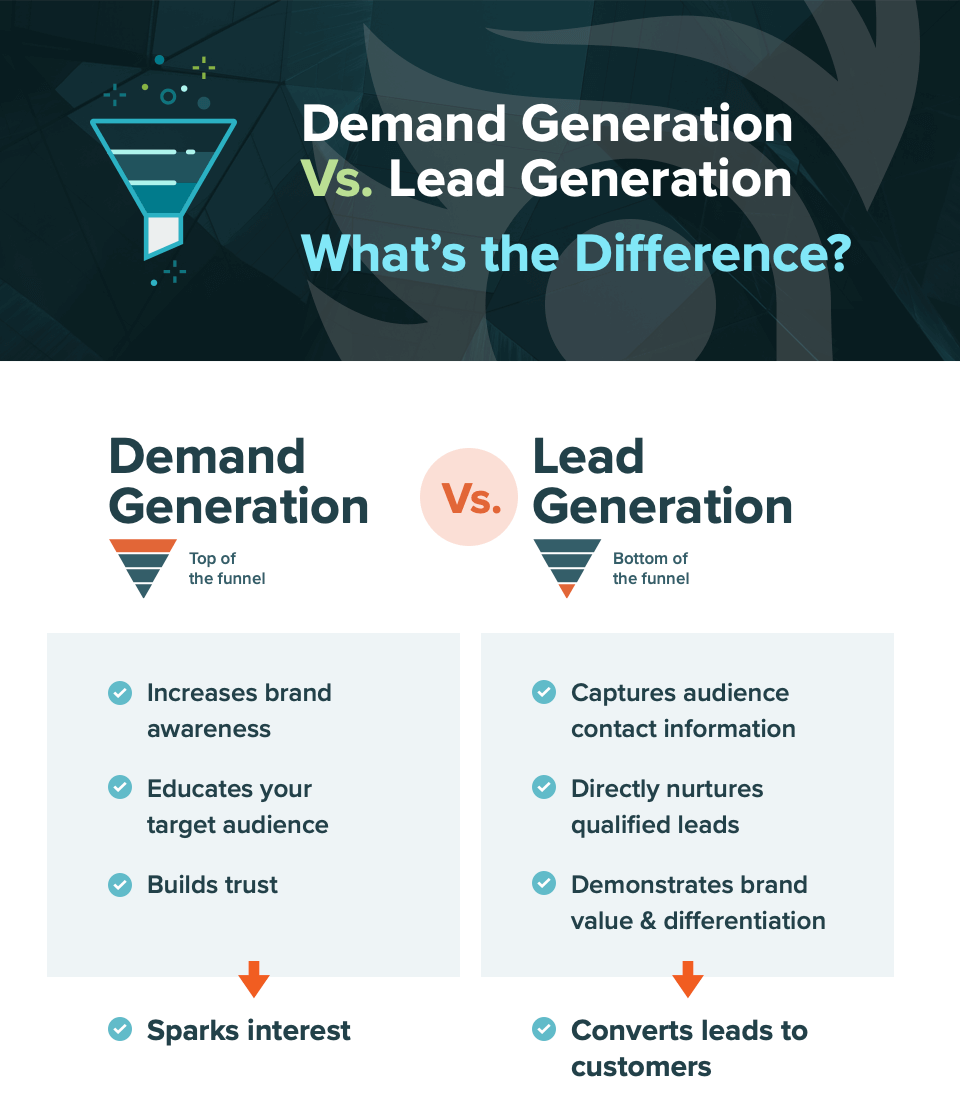
Within the realm of marketing, demand generation and lead generation are often used synonymously, but they have distinct meanings and roles. Understanding these strategies is crucial for effectively targeting ideal customers and boosting sales. Quick Overview of Demand Generation vs. Lead Generation Demand Generation – Top of the funnel (TOFU) Lead Generation -Bottom of […]
7min3716
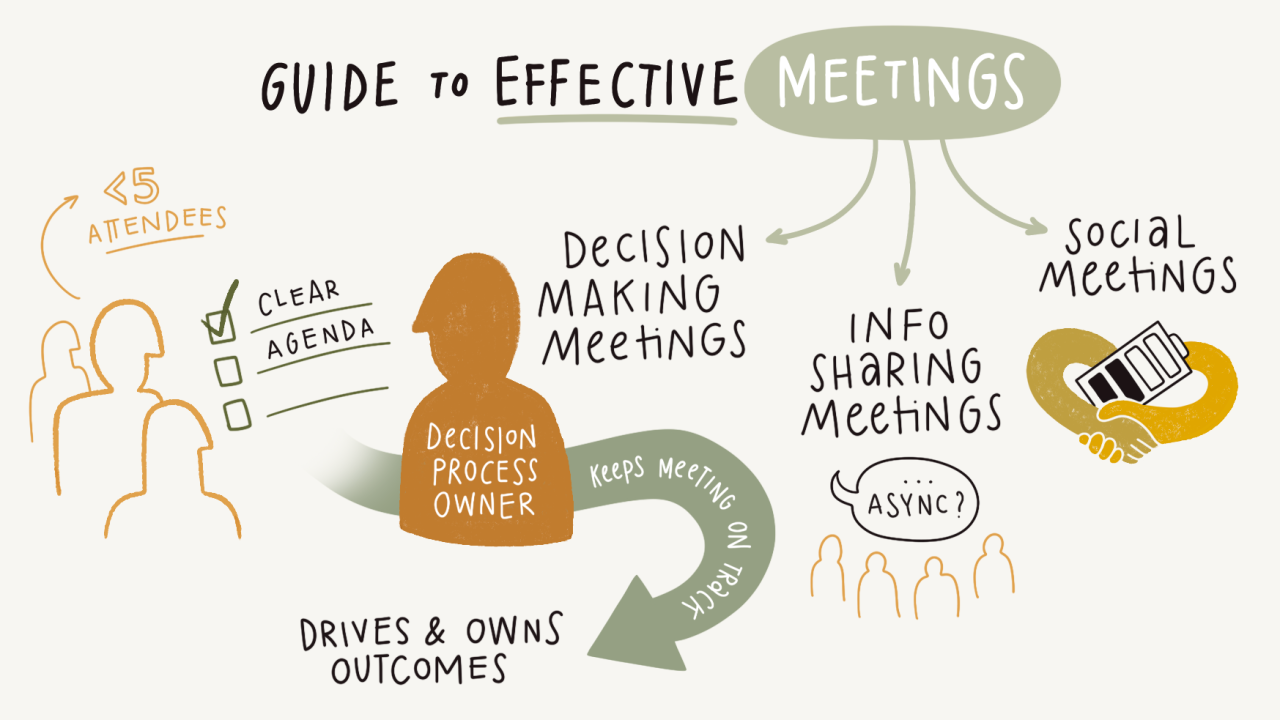
This is about internal business meetings, not meetings with prospects, customers, or third parties. The biggest frustration is when meetings drag on endlessly, leaving tasks unfinished. People often complain, saying, ‘Yes, but we talked about that…’ . A symptom of unproductive meetings. Based on my experience, internal business meetings can be divided into two […]
8min2757
In the rapidly evolving landscape of cybersecurity, businesses face an ever-increasing array of threats that can compromise sensitive data and disrupt operations. Cyber insurance has become a critical component of risk management strategies, offering a financial safety net in the event of a cyber incident. However, the role of cyber insurance companies extends far beyond […]
8min3226
In the 2010’s Endpoint Detection and Response (EDR) was a groundbreaking innovation. Companies like CrowdStrike played a pivotal role in advancing cybersecurity, and their contributions were invaluable. However, as the cybersecurity landscape has evolved, the solutions offered by CrowdStrike, SentinelOne, and similar companies have become insufficient. Today’s threats are more sophisticated, breaches are more severe, […]
7min3183
In the rapidly evolving landscape of cybersecurity, no vendor should claim their product is effective unless they are transparent with their users and release their Cyber Transparency Metrics. At Xcitium, we believe that transparency and accountability are paramount. This is why we are inviting our competitors, CrowdStrike and SentinelOne, to follow our lead and publicly […]
7min2675
Whoever runs fast wins the race! In today’s hyper-competitive business landscape, companies are constantly seeking ways to gain an edge over their rivals. One of the most effective strategies for achieving this is by accelerating the pace at which they run the Deming Cycle, also known as the PDCA (Plan-Do-Check-Act) cycle. This iterative process of […]
11min2866
In many organizations, the sales and marketing teams often find themselves at odds over the quality of leads being passed along the sales pipeline. A common refrain from sales teams is that marketing fails to deliver leads that are genuinely ready for sales engagement. This friction, while commonplace, stems largely from a fundamental misalignment: a […]
18min3056
1. Getting Attention of a Potential Customer Getting the attention of potential customers is primarily about capturing their attention and making them aware of your product or service. Here are some common steps involved: Identify the Target Audience: Understand who your potential customers are, including their demographics, interests, and needs. This step is crucial for […]